How to synchronize users and groups from Active Directory (including passwords) to virtually anything
September 2012.
The situation
You have an Active Directory server with users and groups. You would like those to be synchronized with something else, be it a sql database, an openldap server, a text file, a samba passdb file, etc.
What you need
To achieve this, you will need:
Roles installed on your AD Server: Identity Management for Unix (including password synchronization and administration tools).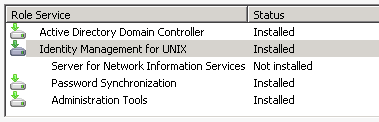
- A script to fetch the users and the groups from AD using the LDAP protocol.
- A script that will act as an SSO daemon to be able to synchronize passwords as well. (see http://support.microsoft.com/kb/324542 for more information on the subject). With this, you won't be able to extract the passwords currently stored in the AD server, but you will be notified of any change.
Download, install and configure pSSOd
pSSOd is a collection of perl scripts that provide the synchronization we want.
You can find the scripts on github at: https://github.com/ZeWaren/pSSOd.
In this example, the following hosts are involved:
- 192.168.42.10: Windows Server 2008 R2.
- 192.168.42.20: Debian Squeeze.
Configure password synchronization on the Windows host
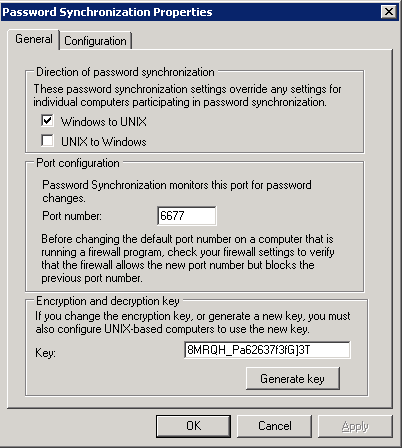
- Configure the properties of Password Synchronization
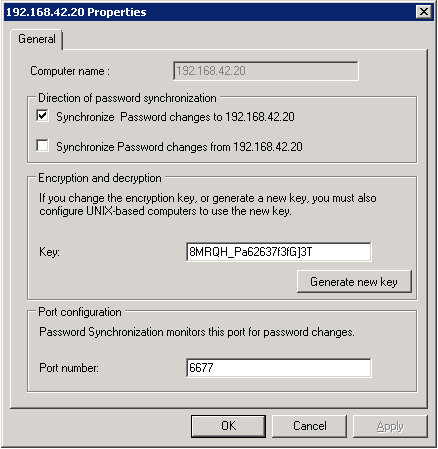
- Add an UNIX computer and configure its properties.
Configure and run perlsync
Configure and run perlsync.pl to fetch everything you need except the passwords.
Configure:
use constant LDAP_HOST => "192.168.42.10";
use constant LDAP_USER => "aduser\@grandopen.zwm.fr";
use constant LDAP_PASSWORD => "abcd1234___";
use constant LDAP_BASE => "DC=grandopen,DC=zwm,DC=fr";
Run:
root@debiantest:~# perl perlsync.pl
$VAR1 = {
'CN=User One,CN=Users,DC=grandopen,DC=zwm,DC=fr' => {
'name' => 'User One',
'accountname' => 'uone'
},
'CN=Guest,CN=Users,DC=grandopen,DC=zwm,DC=fr' => {
'name' => 'Guest',
'accountname' => 'Guest'
},
'CN=AD User,CN=Users,DC=grandopen,DC=zwm,DC=fr' => {
'name' => 'AD User',
'accountname' => 'aduser'
},
[...]
};
$VAR1 = {
'Even Users' => {
'users' => [
'usix',
'ufour',
'utwo'
],
'description' => 'Users that have an even id'
},
'Group two' => {
'users' => [
'usix',
'ufive',
'ufour'
],
'description' => 'This is the second group'
},
[...]
};
Configure and start perlssod
Configure and start perlssod.pl in order to be notified of any password change.
Configure:
use constant SSOD_SECRET => "8MRQH_Pa62637f3fG]3T";
use constant SSOD_TCP_HOST => "192.168.42.20";
use constant SSOD_TCP_PORT => 6677;
use constant SSOD_DEBUG_MODE => 0;
Be sure to allow TCP connections between the two hosts, on port 6677.
Watch /var/log/pssod.log to know what is happening.
root@debiantest:/var/log# tail -f pssod.log
2012/09/11 15:52:59 INFO Starting pSSOd.
2012/09/11 15:53:19 INFO Calling callback with user ufour.
2012/09/11 15:53:19 INFO Inside callback with user ufour and password abcd1234$!!.
Complete the scripts
If everything works correctly, you now have a way to fetch the users and groups from the AD server, and a way to be notified of any password change.
You can now complete perlssod.pl and perlsync.pl to store the information where you need it.
Example scripts
Some example scripts are provided in the syncs_and_callbacks folder of pSSOd, to store the information into:
- A SQL database (MySQL, Postgres, SQLite and whatever DBI supports)
- Some htpasswd and htgroups files
Also, you can obviously build you own scripts depending on your needs.